
December 20, 2019 11:25 by
 Peter
Peter
Do you ever encountered an error if you deploying WebSocket server application which targeted .NET 4.5 to Windows Server 2012 plus IIS 8? Yes, it was an exception shown in browser whenever tried to open a web page. The exception said:
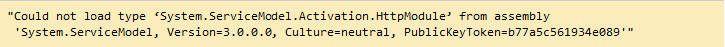
This problem is: the default configuration in applicationHost.config (in C:\Windows\System32\inetsrv\config) declared two conflicted modules and two conflicted handlers:
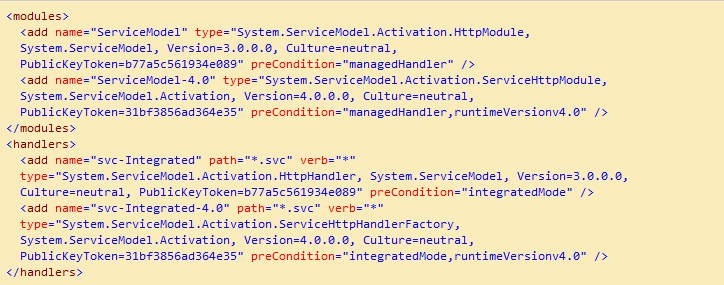
As we know, applicationHost.config contains the root settings for all web sites and web applications on the server. Therefore, any web application would have all the four conflicted modules and handlers loaded by default. “ServiceModel” and “svc-Integrated” were for .NET Activation 3.x while “ServiceModel-4.0” and “svc-Integrated-4.0” were for .NET Activation 4.x. Unfortunately, the 3.x items were declared before the 4.x items. That was why the exception occurred for a .NET 4.x web application!
Then how did such a situation happen? On Windows Server 2008, it could happen when you install .NET 3.x framework or IIS 7.5 with Activation features after .NET framework 4.x is installed. However, on Windows Server 2012, it always happens when you install .NET framework 3.x with Activation features.

Microsoft officially announced the solution (http://support.microsoft.com/kb/2015129) for Windows Server 2008 plus IIS 7.5: manually running “aspnet_regiis.exe /iru” for .NET framework 4.x (in C:\Windows\Microsoft.NET\Framework\v4.0.30319 or C:\Windows\Microsoft.NET\Framework64\v4.0.30319). However, aspnet_regiis.exe is not allowed to run for IIS 8.
The final solution was to delete the 3.x module and handler from IIS manager. You could delete them at the application or site level if you want to keep them in applicationHost.config. But if you wanted to delete them from applicationHost.config. So you should did the following steps:
1. In IIS manager, click the machine name node.
2. In “Features View”, double-click “Modules”.
3. Find “ServiceModel” and remove it.
4. Go back to the machine name node’s “Features View”, double-click “Handler Mappings”.
5. Find “svc-Integrated” and remove it.
Now everything works well.

September 18, 2013 08:17 by
 Ronny
RonnyThis error means that the private key does not match the public key (the .crt file). The keypair is not successfully joined into a working SSL certificate.
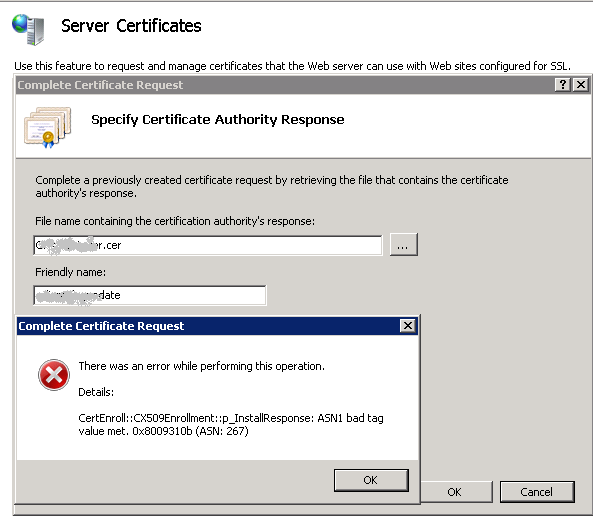
Here solution to resolve this error
1. (Start button -> RUN -> Type : MMC)
2. Choose Tab “File”
3. Add/Remove Snap-ins -> certificates and click “Add >”.
4. Select “Computer account” and Finish. OK

5. Personal > Certificates > right-click and select All Tasks > select Import > guide to the .crt file.)
6. Double-click the crt certificate file you just imported -> select the Details tab, scroll all the way down to Thumbprint and highlight Thumbprint.
7. In the lower pane, block and copy all the letters of the thumbprint. Paste the thumbprint characters into notepad. Open the command prompt and run this command: Certutil /?
8. The command you’ll want to run is:
certutil -repairstore my “{PASTE THE CODE }”
9. When you see “CertUtil: -repairstore command completed successfully” the private key will be associated with the .CRT file in the personal store. The certificate should show up in IIS 7.5 under Server Certificates.
10. Now you should be able to assign the SSL certificate to the appropriate website(s).

January 26, 2012 05:35 by
 Scott
ScottThis is the error message that sometimes you can find on IIS:
Server Error in ‘/’ Application.
Configuration Error
Description: An error occurred during the processing of a configuration file required to service this request. Please review the specific error details below and modify your configuration file appropriately.
Parser Error Message: It is an error to use a section registered as allowDefinition=’MachineToApplication’ beyond application level. This error can be caused by a virtual directory not being configured as an application in IIS.
I will gonna show you how to fix this issue. What is the issue?
1. When you create an new web application using visual studio.net, it automatically creates the virtual directory and configures it as an application. However, if you manually create the virtual directory and it is not configured as an application, then you will not be able to browse the application and may get the above error. The debug information you get as mentioned above, is applicable to this scenario.
To resolve it, Right Click on the virtual directory - select properties and then click on "Create" next to the "Application" Label and the textbox. It will automatically create the "application" using the virtual directory's name. Now the application can be accessed.
2. When you have sub-directories in your application, you can have web.config file for the sub-directory. However, there are certain properties which cannot be set in the web.config of the sub-directory such as authentication, session state (you may see that the error message shows the line number where the
authentication or sessionstate is declared in the web.config of the sub-directory). The reason is, these settings cannot be overridden at the sub-directory level unless the sub-directory is also configured as an application (as mentioned in the above point).
Mostly we have the practice of adding web.config in the sub-directory if we want to protect access to the sub-directory files (say, the directory is admin and we wish to protect the admin pages from unathorized users).
But actually, this can be achieved in the web.config at the application's root level itself, by specifing the location path tags and authorization, as follows:-
<location path="Admin">
<system.web>
<authorization>
<allow roles="administrators" />
<deny users="*" />
</authorization>
</system.web>
</location>
However, if you wish to have a web.config at the sub-directory level and protect the sub-directory, you can just specify the Authorization mode as follows:-
<configuration>
<system.web>
<authorization>
<allow roles="administrators" />
<deny users="*" />
</authorization>
</system.web>
</configuration>
Thus you can protect the sub-directory from unauthorized access.